Cybersecurity


INTRODUCTION
In today’s digital age, where technology has become an integral part of our lives, the need for cybersecurity has never been more crucial. With the increasing number of cyber threats and attacks, it is essential to have a solid understanding of cybersecurity principles and practices. This essay introduces cybersecurity by discussing its importance, key concepts, and strategies.
Cybersecurity protects computer systems, networks, and data from unauthorized access or damage. It encompasses various measures to prevent cyber threats like hacking, phishing, malware attacks, and data breaches. The importance of cybersecurity cannot be overstated, as it safeguards sensitive information and ensures the smooth functioning of organizations.
One key concept in cybersecurity is confidentiality. Confidentiality ensures that only authorized individuals have access to sensitive information. This is achieved through encryption techniques that scramble data so that it can only be deciphered by those with the proper decryption keys. By maintaining confidentiality, organizations can protect their trade secrets, customer data, and other valuable information from falling into the wrong hands.
Another crucial concept in cybersecurity is integrity. Integrity ensures that data remains unaltered throughout its lifecycle. It involves checksums and digital signatures that detect any unauthorized modifications or tampering with data. By ensuring integrity, organizations can trust the accuracy and reliability of their data.
Availability is another fundamental aspect of cybersecurity. Availability ensures that computer systems and networks are accessible when needed. This involves implementing redundancy measures such as backup systems or failover mechanisms to ensure continuous operation despite hardware failures or cyber-attacks.
Organizations employ various strategies in their cybersecurity practices to effectively address cyber threats. One common strategy is risk assessment and management. This involves identifying potential vulnerabilities within a system or network through regular audits or penetration testing and taking appropriate measures to mitigate those risks.
Another strategy employed in cybersecurity is user awareness training. Since many cyber-attacks rely on human error, educating users about best practices, such as strong password management and recognizing phishing emails, is crucial in preventing successful attacks.
Furthermore, organizations often implement firewalls and intrusion detection systems to monitor network traffic and identify suspicious activity. These tools act as a first line of defense by blocking unauthorized access attempts or alerting administrators to potential threats.
Organizations can protect their valuable information from cyber threats by understanding confidentiality, integrity, and availability. Implementing risk assessment and user awareness training strategies further enhances cybersecurity practices. As technology advances, individuals and organizations must prioritize cybersecurity to ensure a safe and secure digital environment.
Executive Diploma In Cybersecurity
The field of cybersecurity has become increasingly important in our digital age. With the rise of cyber threats and attacks, organizations are recognizing the need for professionals who can protect their sensitive information and systems from potential breaches.
Many educational institutions now offer executive diploma programs in cybersecurity to meet this demand.
An executive diploma in cybersecurity is a specialized program designed for professionals with experience in the field or related industries.
It provides them with advanced knowledge and skills to effectively manage and mitigate cyber risks within their organizations. The program typically covers many topics, including network security, data protection, incident response, ethical hacking, risk assessment, and compliance.
One key aspect of an executive diploma program is its focus on practical application. Unlike traditional academic degrees that may emphasize theory and research, an executive diploma program prioritizes hands-on training and real-world scenarios.
Students must often complete projects or case studies that simulate cyber threats or attacks. This approach allows participants to develop critical thinking skills and practical experience dealing with complex cybersecurity issues.
Another essential feature of an executive diploma program is its flexibility. These programs are specifically designed for working professionals who may need more time or resources to pursue a full-time degree.
They are often offered as part-time or online courses, allowing students to balance their work commitments while acquiring new skills and knowledge in cybersecurity.
An executive diploma program’s curriculum typically includes technical and non-technical subjects. Specialized courses cover network security protocols, cryptography algorithms, secure coding practices, and penetration testing techniques.
Non-technical courses focus on risk management strategies, legal frameworks for cybersecurity, policy development, and incident response planning.
One significant advantage of pursuing an executive diploma in cybersecurity is the career opportunities it opens up.
As organizations continue to prioritize data protection and risk management, there is a growing demand for qualified professionals who can lead cybersecurity initiatives within companies across various industries. Graduates of these programs can find employment as cybersecurity analysts, consultants, managers, or even chief information security officers (CISOs).
An executive diploma in cybersecurity is a specialized program that equips professionals with the necessary skills and knowledge to protect organizations from cyber threats.
It offers practical training, flexibility, and a comprehensive curriculum that covers both technical and non-technical aspects of cybersecurity.
With the increasing importance of data protection and risk management in today’s digital landscape, pursuing an executive diploma in cybersecurity can provide individuals with valuable career opportunities in this rapidly growing field.

The Purpose Of These Lectures And Its Significance
In today’s digital age, cybersecurity has become a critical concern for individuals, organizations, and governments.
Cyber-attack threats have grown exponentially with the increasing reliance on technology and the internet.
This lecture explores the purpose of cybersecurity and its significance in protecting sensitive information, maintaining privacy, and ensuring the smooth functioning of various sectors.
The primary purpose of these lectures is to shed light on the importance of cybersecurity in safeguarding personal data and sensitive information. With the rise in online transactions, social media usage, and cloud storage systems, individuals are constantly sharing their details online.
From banking information to medical records, our digital presence contains valuable data that cybercriminals can exploit.
By understanding the significance of cybersecurity measures such as encryption protocols, firewalls, and secure authentication methods, individuals can take steps to protect themselves from potential threats.
Furthermore, this lecture aims to emphasize the role of cybersecurity in maintaining privacy. In an era where surveillance technologies are becoming increasingly sophisticated, ensuring that our online activities remain private is crucial.
Cybersecurity measures are vital in protecting our digital footprints from unauthorized access or surveillance by state actors and malicious hackers.
By highlighting the significance of encryption techniques and secure communication channels like virtual private networks (VPNs), this essay seeks to raise awareness about preserving privacy rights in an interconnected world.
Moreover, this study recognizes the broader significance of cybersecurity for organizations across various sectors.
Businesses today heavily rely on technology infrastructure for their operations – from financial institutions handling sensitive customer data to manufacturing plants controlling critical systems through interconnected networks.
A single cyber-attack can have devastating consequences for these organizations and society. By addressing topics such as network security protocols, incident response strategies, and employee training programs on cybersecurity best practices, this essay aims to underscore how investing in robust cybersecurity measures is crucial for organizations’ smooth functioning and sustainability.
This lectures aim to highlight cybersecurity’s significance in protecting personal information, maintaining privacy, and ensuring the smooth functioning of organizations.
With the increasing reliance on technology and interconnected systems, cyber-attacks have become a significant threat.
By understanding the importance of cybersecurity measures such as encryption protocols, secure communication channels, and employee training programs, individuals and organizations can take proactive steps to mitigate risks and safeguard their digital assets.
In an era where our lives are increasingly intertwined with technology, prioritizing cybersecurity has never been more critical.
https://youtu.be/1vV0t2XbtuU
The evolving threat landscape in cybersecurity is marked by dynamic changes in the nature and sophistication of cyber threats, requiring constant adaptation and vigilance to safeguard digital assets. Traditional threats such as malware, phishing, and denial-of-service (DoS) attacks persist but have evolved to become more targeted and technically advanced. Cybercriminals employ sophisticated techniques to exploit vulnerabilities, aiming for financial gain, data theft, or disruption of services.
Advanced Persistent Threats (APTs) represent a significant facet of the evolving landscape. These are prolonged and targeted cyberattacks, often orchestrated by nation-state actors or well-funded groups. APTs involve a combination of stealthy infiltration, prolonged surveillance, and data exfiltration, posing a severe challenge for organizations aiming to defend against these persistent and often covert threats.
Insider threats contribute to the complexity of the landscape. Malicious insiders may intentionally compromise security, while unintentional risks arise from employees’ inadvertent actions, such as falling victim to phishing attacks. Organizations must balance the need for trust with robust access controls, monitoring, and employee awareness to mitigate these internal risks effectively.
Technological advancements play a dual role in shaping the threat landscape. Cloud computing, while providing scalability and flexibility, introduces new security challenges. The shared responsibility model demands that organizations and cloud service providers collaborate to secure data and applications. Similarly, the proliferation of Internet of Things (IoT) devices expands the attack surface, requiring heightened security measures to protect interconnected devices.
Social engineering remains a potent threat vector, relying on manipulating human psychology rather than exploiting technical vulnerabilities. Techniques like phishing, where attackers impersonate trustworthy entities to trick individuals into revealing sensitive information, continue to evolve with increased sophistication.
The cybersecurity landscape is further complicated by the rapid pace of technological change. Emerging technologies like artificial intelligence (AI) and machine learning (ML) are employed both by cybersecurity defenders and attackers. While AI enhances threat detection through behavioral analysis and anomaly detection, cybercriminals leverage these technologies to automate and enhance their attacks.
International cooperation becomes crucial in the face of global cyber threats. Information sharing and collaboration on cybersecurity issues foster a collective defense against malicious actors. However, geopolitical tensions and differing perspectives on cybersecurity practices can pose challenges to effective international collaboration.
Looking ahead, the landscape is expected to witness the impact of quantum computing, raising concerns about the adequacy of current encryption methods. The rollout of 5G networks introduces new security challenges, particularly in ensuring the integrity and confidentiality of data transmitted over these high-speed networks. Cybersecurity in autonomous systems, including self-driving vehicles and smart infrastructure, presents a frontier for potential vulnerabilities.
In conclusion, the evolving threat landscape demands a multifaceted approach to cybersecurity. Organizations must stay abreast of emerging threats, invest in cutting-edge technologies, foster a cybersecurity-aware culture, and collaborate globally to fortify their defenses against the ever-changing tactics of cyber adversaries.
Traditional cyber threats continue to pose significant risks in the ever-evolving landscape of cybersecurity. Among these, malware remains a persistent and pervasive threat. Malicious software is designed to infiltrate computer systems with the intent of causing harm, whether through data theft, system disruption, or unauthorized access. Viruses, worms, trojans, ransomware, and spyware represent various forms of malware, each exploiting different vulnerabilities and attack vectors.
Phishing, another prevalent traditional threat, relies on social engineering to deceive individuals into divulging sensitive information such as usernames, passwords, or financial details. Phishing attacks often take the form of seemingly legitimate emails, messages, or websites that trick users into providing confidential data. This method continues to be a favored tactic for cybercriminals due to its effectiveness and adaptability.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks target the availability of systems and networks. DoS attacks overwhelm a single target with traffic, rendering it inaccessible, while DDoS attacks leverage multiple compromised devices to orchestrate a coordinated assault. These attacks can disrupt online services, causing financial losses and reputational damage for businesses.
Advanced Persistent Threats (APTs) represent a more sophisticated and targeted form of cyber threat. APTs involve prolonged and covert attacks by well-funded adversaries, often nation-state actors or advanced cybercrime groups. These threats are characterized by careful planning, persistent unauthorized access, and a focus on specific objectives, such as espionage or stealing sensitive data.
Insider threats, both intentional and unintentional, add another layer of complexity to cybersecurity. Malicious insiders with access to sensitive information can intentionally compromise security, while unintentional threats may arise from employees who inadvertently fall victim to phishing scams or unknowingly engage in risky behaviors that expose the organization to cyber risks.
Zero-day exploits target vulnerabilities in software or hardware before developers can release patches. Cybercriminals exploit these vulnerabilities to gain unauthorized access, install malware, or execute other malicious activities. The race between attackers discovering and exploiting zero-days and developers creating and deploying patches creates a constant challenge for cybersecurity professionals.
In addressing these traditional cyber threats, organizations must implement a comprehensive cybersecurity strategy. This includes regular software updates to patch known vulnerabilities, employee training programs to raise awareness about phishing and social engineering, and the deployment of security measures such as firewalls and antivirus software. The landscape may evolve, but these foundational measures remain critical for mitigating the risks posed by traditional cyber threats.
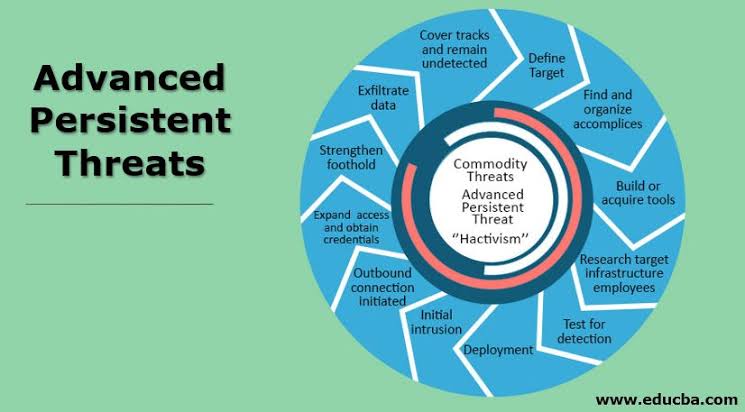
Advanced Persistent Threats (APTs) constitute a highly sophisticated and targeted category of cyber attacks that transcend conventional cybercriminal activities. These strategic campaigns are orchestrated by well-funded and adept adversaries, often harboring motives such as corporate espionage, intellectual property theft, or unauthorized access to sensitive information. To effectively navigate the evolving cyber landscape, organizations must grasp the distinctive characteristics and strategies associated with APTs.
APTs distinguish themselves through their prolonged focus on specific targets, in contrast to opportunistic attacks. This longevity allows attackers to engage in meticulous planning and reconnaissance, aligning their efforts with precise objectives rather than seeking easily exploitable vulnerabilities.
A key feature of APTs is their commitment to covert operations. Adhering to a principle of stealth and discretion, attackers strive to remain undetected for extended periods. This clandestine approach enables them to gather intelligence or execute their goals without raising suspicion, challenging conventional detection methods.
The techniques employed in APTs are characterized by their sophistication. Attackers leverage advanced methods, including custom malware, zero-day exploits, and evasion tactics designed to circumvent traditional security measures. This complexity renders APTs difficult to detect through standard cybersecurity tools, necessitating a proactive and adaptive defense approach.
Targeted organizations play a pivotal role in APTs, with adversaries selecting specific entities possessing valuable assets, intellectual property, or sensitive information. Industries such as government, defense, finance, and technology are frequent targets due to the potential high value of the data they hold.
APTs utilize multiple attack vectors, blending social engineering, spear-phishing, and other tactics. They may compromise third-party vendors or initiate supply chain attacks to gain access to the primary target. This multifaceted approach enhances the attackers’ chances of success.
The involvement of nation-state actors is another hallmark of APTs. In certain instances, these campaigns align with geopolitical or economic agendas, introducing implications that extend beyond individual organizations to impact international relations and cybersecurity norms.
Maintaining persistent access is a primary objective of APTs. Once inside a target network, attackers establish backdoors and stealthy communication channels, ensuring their ability to re-enter the compromised system even if initially detected and removed.
Information gathering is a fundamental aspect of APTs, with attackers focusing on collecting valuable data over time. This may include sensitive business plans, intellectual property, personal data, or classified government information, depending on the attackers’ motives.
Customized tools are frequently deployed by APTs, designed specifically for the target environment. This customization reduces the likelihood of detection by standard security solutions that rely on known signatures.
As APTs continuously evolve, adapting to changing circumstances and security measures, organizations must adopt a comprehensive cybersecurity approach. This includes continuous monitoring, threat intelligence sharing, employee training, and the implementation of advanced security technologies capable of detecting and responding to sophisticated, persistent threats. Regular security audits and assessments are essential components of an effective defense strategy, enabling organizations to identify and address potential vulnerabilities before they can be exploited by APTs.

Cloud computing refers to the delivery of computing services—such as storage, processing power, and applications—over the internet. These services are provided by third-party providers who maintain and manage the necessary infrastructure. Cloud computing offers several benefits, such as scalability, flexibility, and cost-efficiency. However, it also introduces unique cybersecurity challenges that organizations must address to ensure the security of their data and systems.
One key aspect is data security. Cloud providers store vast amounts of data from multiple users on shared infrastructure. Ensuring the security and privacy of this data is a paramount concern. Organizations need robust encryption mechanisms to protect data both in transit and at rest.
Another critical consideration is Identity and Access Management (IAM). Managing user access and permissions in a cloud environment is crucial. Effective IAM policies help prevent unauthorized access and ensure that users have appropriate permissions only for the resources they need.
Cloud services often follow a shared responsibility model. While the cloud provider secures the infrastructure, organizations are responsible for securing their data, applications, and configurations. Understanding and implementing this model is essential for effective cybersecurity.
Compliance and legal concerns are significant considerations in cloud computing. Many industries have specific regulatory requirements regarding data protection and privacy. Organizations using cloud services must ensure compliance with relevant regulations and standards, requiring careful consideration of data residency, handling, and access controls.
In the event of a security incident, incident response and forensics become crucial. Organizations need well-defined processes to detect, respond to, and recover from security breaches. Cloud environments add complexity to these processes, requiring coordination between the organization and the cloud service provider to investigate and mitigate incidents effectively.
In conclusion, while cloud computing offers numerous advantages, organizations must be diligent in addressing cybersecurity challenges. This involves implementing robust security measures, understanding the shared responsibility model, and staying abreast of compliance requirements. By doing so, organizations can leverage the benefits of the cloud while maintaining the confidentiality, integrity, and availability of their data and systems.
The Internet of Things (IoT) has emerged as a significant area of concern in the realm of cybersecurity due to the increased attack surfaces it introduces. With the proliferation of interconnected devices in various environments, from smart homes to industrial systems, the attack surface expands exponentially. This expanded attack surface provides cyber adversaries with more entry points and potential vulnerabilities to exploit. The sheer volume and diversity of IoT devices, ranging from smart thermostats to industrial sensors, create a complex ecosystem that demands careful attention to security.
One of the primary challenges associated with IoT in the context of cybersecurity is the prevalence of insecure IoT devices. Many IoT devices are developed with a focus on functionality and cost, often at the expense of robust security features. This lack of security measures makes these devices susceptible to exploitation, potentially serving as entry points for cyber attackers. Vulnerabilities in insecure IoT devices can lead to unauthorized access, data breaches, or even compromise the entire network they are connected to, underscoring the critical need for enhanced security measures in IoT device development and deployment.
In addressing the cybersecurity implications of IoT, it becomes imperative for manufacturers, developers, and users to prioritize security considerations. Implementing strong authentication mechanisms, encrypting communication channels, and regularly updating device firmware are essential steps to mitigate the risks associated with the increased attack surfaces and insecure nature of many IoT devices. As IoT continues to evolve, a proactive and collaborative approach to cybersecurity is essential to ensure the integrity and privacy of the interconnected systems facilitated by IoT technologies.
The Need For Trained Professionals In Cybersecurity
In today’s digital age, the need for trained professionals in cybersecurity has become more critical than ever before.
With the increasing reliance on technology and the growing threat of cyberattacks, organizations and individuals alike are vulnerable to potential breaches that can have devastating consequences.
This essay will highlight the importance of trained professionals in cybersecurity and why their expertise is essential in safeguarding our digital infrastructure.
Firstly, it is crucial to understand the evolving nature of cyber threats. Hackers and cybercriminals constantly develop new techniques to exploit computer systems, networks, and software vulnerabilities.
These attacks can range from stealing sensitive information to disrupting critical infrastructure or even causing financial losses.
Trained professionals in cybersecurity possess the knowledge and skills required to identify these vulnerabilities proactively and implement effective countermeasures to mitigate potential risks.
Secondly, trained professionals play a vital role in preventing data breaches.
In recent years, there have been numerous high-profile cases where the personal information of millions of individuals was compromised due to inadequate security measures.
Such incidents result in financial losses and erode public trust in organizations’ ability to protect their data.
Organizations can significantly reduce the risk of data breaches by employing trained cybersecurity experts who understand best practices for securing networks, implementing encryption protocols, and conducting regular audits.
Furthermore, trained professionals are essential for incident response and recovery after a cyberattack.
In case of a breach or system compromise, immediate action is necessary to minimize damage and restore normal operations swiftly. Cybersecurity experts possess specialized knowledge about forensic analysis techniques that can help identify the source of an attack and gather evidence for legal proceedings if required.
They also have experience implementing incident response plans effectively, ensuring that any damage caused by an attack is promptly contained.
Moreover, as technology continues to advance rapidly across various industries such as healthcare, finance, transportation, and government sectors – so does the need for skilled cybersecurity professionals within these fields.
Integrating Internet-of-Things (IoT) devices, cloud computing, and artificial intelligence has expanded the attack surface for cybercriminals.
Trained professionals are needed to assess the security implications of these technologies and develop robust strategies to protect them from potential threats.
The need for trained professionals in cybersecurity must be balanced. Their expertise is vital in safeguarding our digital infrastructure, preventing data breaches, and responding effectively to cyberattacks.
As technology advances and cyber threats become more sophisticated, organizations must prioritize investing in cybersecurity talent. By doing so, they can mitigate risks, protect sensitive information, and maintain public trust in an increasingly interconnected world.


OVERVIEW ON CYBERSECURITY
Over the past few decades, the evolution of cybersecurity has unfolded through distinct generations, each marked by technological advancements and corresponding security challenges. The first generation, characterized by the advent of computers and networking, saw a focus on perimeter defense through firewalls and antivirus software. However, the emphasis on preventing external threats proved insufficient as attackers developed more sophisticated methods, leading to the recognition that a holistic approach encompassing not just external threats but also insider risks was necessary.
The second generation of cybersecurity witnessed the rise of proactive defense mechanisms. Intrusion detection systems, encryption, and the establishment of security protocols became prominent features. This era marked a shift from merely preventing attacks to actively monitoring and responding to security incidents. As cyber threats evolved in complexity, this generation emphasized continuous monitoring, incident response planning, and the importance of user awareness. The integration of security into system design and the recognition of the human factor in cybersecurity became key themes, laying the groundwork for a more dynamic and adaptive approach to protecting digital assets.
MANIPULATION TECHNIQUES
Phishing Emails
Phishing emails are a prevalent form of social engineering, aiming to manipulate individuals into divulging sensitive information. Attackers often employ psychological tactics to create a sense of urgency or fear, compelling recipients to act impulsively. Crafty manipulations may involve posing as a trustworthy entity, such as a bank or employer, to gain victims’ trust.
These emails commonly exploit human tendencies, like curiosity or the desire for reward, by including enticing subject lines or offers. Cybersecurity trainees must learn to recognize red flags, such as generic greetings, unusual sender addresses, or misspellings, as these can signal potential phishing attempts.
Moreover, attackers may use sophisticated techniques like spear-phishing, tailoring messages to specific individuals based on gathered information. It is crucial for trainees to understand the importance of verifying sender legitimacy and avoiding clicking on suspicious links or downloading attachments.
By fostering a heightened awareness of these manipulation tactics, you can enhance your ability to detect and thwart phishing attempts, contributing to a more secure online environment.

Impersonation attacks
involve perpetrators posing as someone else to deceive and manipulate individuals or systems. In the digital realm, these attacks can take various forms, such as email spoofing or social engineering.
One common example is CEO fraud, where an attacker impersonates a high-ranking executive within a company. The attacker might send an urgent email to an employee, typically in the finance department, requesting a large fund transfer. This manipulation preys on the authority associated with the executive’s position, aiming to bypass regular checks.
In a broader context, attackers may impersonate trusted entities like government agencies or service providers, exploiting the credibility associated with these sources. These manipulative tactics often involve creating convincing replicas of websites or emails to deceive unsuspecting individuals.
Cybersecurity professionals need to be vigilant against impersonation attacks, employing multi-factor authentication, verifying email sender addresses

PSYCHOLOGICAL TACTICS
Psychological tactics play a crucial role in cyber attacks, with two notable strategies being pretexting and baiting, both of which exploit human behavior for malicious purposes.
*Pretexting:*
Pretexting involves creating a fabricated scenario or pretext to manipulate individuals into divulging sensitive information. In cybersecurity, attackers might masquerade as trustworthy entities, such as IT support or colleagues, to trick targets into sharing confidential data. This tactic relies heavily on social engineering skills, where the attacker crafts a convincing narrative to gain the victim’s trust. For instance, a pretexting attacker may pose as a company executive seeking urgent access to privileged information, leveraging the guise of authority to manipulate the victim.
Cybersecurity awareness training is vital in combating pretexting. Employees must be educated on verifying identities and confirming requests through proper channels before sharing sensitive information. Establishing a culture of skepticism and caution can significantly mitigate the success of pretexting attacks.
*Baiting:*
Baiting involves enticing individuals with something desirable to trick them into compromising security. In the cyber realm, this often takes the form of malware-infected files or malicious links disguised as appealing content. For instance, attackers may leave infected USB drives in a public space labeled as “Employee Bonuses” or share enticing download links through email. Once the bait is taken, malware infiltrates the system, potentially leading to data breaches or system compromise.
To defend against baiting, cybersecurity measures must include robust antivirus software, regular system updates, and user training to recognize and avoid clicking on suspicious links or downloading unfamiliar files. Emphasizing the risks associated with unexpected or tempting offers can bolster resilience against this psychological manipulation tactic.
Understanding and actively countering these psychological tactics are crucial components of a comprehensive cybersecurity strategy, as they address the human element in the ever-evolving landscape of cyber threats.

Cybersecurity Challenges:
The landscape of cybersecurity is fraught with numerous challenges, stemming from the continuous evolution of cyber threats. Malicious actors adapt quickly, employing sophisticated techniques to exploit vulnerabilities in systems. The challenge lies in staying ahead of these threats through proactive measures, robust defense mechanisms, and constant updates to security protocols.
Rapid Technological Changes:
The swift pace of technological advancements poses a significant challenge for cybersecurity practitioners. Emerging technologies, such as artificial intelligence and the Internet of Things (IoT), introduce new attack vectors and vulnerabilities. Securing these innovations requires agile strategies and a keen understanding of potential risks. Cybersecurity teams must adapt swiftly to the evolving tech landscape to maintain effective protection against cyber threats.
Lack of Cybersecurity Awareness:
Human error remains a prevalent factor in cybersecurity incidents. The lack of awareness among users about potential risks, phishing attacks, and secure online practices contributes to the vulnerability of systems. Bridging this awareness gap through comprehensive training programs is essential. Users need to understand the importance of strong passwords, recognize social engineering tactics, and be cautious about sharing sensitive information to bolster the human firewall against cyber threats.
Resource Constraints:
Many organizations face challenges in allocating sufficient resources to cybersecurity efforts. Limited budgets and competing priorities often result in gaps in security infrastructure and personnel. Cybersecurity professionals must navigate these resource constraints by prioritizing risk assessments, focusing on critical assets, and leveraging cost-effective solutions. Collaboration and information-sharing within the cybersecurity community can also help organizations maximize the impact of limited resources.
Addressing these challenges requires a holistic approach that combines technological solutions, user education, and strategic resource allocation. Cybersecurity professionals play a crucial role in navigating these complexities, ensuring the resilience of systems and safeguarding against the ever-evolving landscape of cyber threats.

Adaptive Security Measures:
Adaptive security measures represent a dynamic and responsive approach to cybersecurity, acknowledging the constantly changing nature of threats. Traditional security models are often static, with predefined rules and signatures. In contrast, adaptive security focuses on real-time analysis and adaptive decision-making to identify and mitigate emerging threats.
*Behavioral Analytics:
Adaptive security leverages behavioral analytics to understand the typical patterns of users and systems. By establishing a baseline of normal behavior, any deviations or anomalies can be quickly identified. This proactive approach enables the detection of suspicious activities that may go unnoticed by traditional security measures.
* Machine Learning and AI:
Machine learning and artificial intelligence (AI) are integral components of adaptive security. These technologies enable systems to learn from data, recognize patterns, and autonomously adjust security measures based on evolving threats. Adaptive security systems can continuously improve their ability to detect and respond to new and sophisticated attack methods.
* Continuous Monitoring:
Adaptive security emphasizes continuous monitoring of network traffic, user activities, and system behaviors. This real-time visibility allows security teams to promptly identify and respond to potential threats, reducing the dwell time of attackers within a network.
* User and Entity Behavior Analytics (UEBA):
UEBA plays a crucial role in adaptive security by analyzing the behaviors of both users and entities (devices, applications). By correlating various data points, such as login times, access patterns, and data transfer volumes, UEBA can identify unusual or unauthorized activities, helping prevent insider threats and external attacks.

Threat Intelligence:
Threat intelligence involves gathering, analyzing, and disseminating information about potential cybersecurity threats. It provides organizations with insights into the tactics, techniques, and procedures (TTPs) employed by cyber adversaries, enabling proactive defense strategies.
* Sources of Threat Intelligence:
Threat intelligence can be derived from various sources, including open-source intelligence (OSINT), information shared within the cybersecurity community, government agencies, and commercial threat intelligence feeds. Integrating diverse sources enhances the comprehensiveness of threat intelligence.
* Indicators of Compromise (IoCs):
Threat intelligence often includes IoCs, such as IP addresses, domain names, and malware signatures associated with known threats. Security teams use these IoCs to detect and block malicious activities within their networks.
* Tactics, Techniques, and Procedures (TTPs):
Understanding the TTPs employed by threat actors is critical for effective threat intelligence. By recognizing how adversaries operate, organizations can tailor their defenses to counter specific attack methods, enhancing overall security posture.
Security Orchestration:
Threat intelligence can be integrated into security orchestration platforms to automate responses to known threats. This automation allows for faster and more coordinated incident response, minimizing the impact of cyber attacks.
Adaptive security measures and threat intelligence are complementary components of a modern cybersecurity strategy. Adaptive security enables organizations to dynamically respond to emerging threats, while threat intelligence provides the contextual information needed to make informed decisions and enhance overall cyber resilience.
